Hi all,
Given how untrustworthy and vulnerable CCTV cameras and NVRs might be today, I would like to avoid connecting them directly to the Internet. Thus, I would like to build a custom system and securely connect to it for remote viewing. As networking might not necessarily be my area of expertise, I would like to ask for advice as to the most secure way to have my CCTV system connected to LAN and accessible remotely.
After doing some research, I figured that I should use VLANs to isolate the CCTV cameras and deny Internet access to them. On top of that, I should replace my router with one that provides a VPN server (such as TP-Link Archer BE230 that provides WireGuard) that should be used to remotely connect to my LAN, and hence, access my cameras.
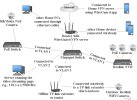
My CCTV system comprises of POE cameras connected to a Reolink NVR, but I am also planning on connecting some Wi-Fi camera (as there is no possible way to run a cable to the area I would like to install it) and a HikVision PoE camera as well. Below I have provided a diagram of how I think the devices should be connected; however, like I said, I am not the expert in this field and that's why I would like to kindly ask for an expert's advice.
Diagram Notes
----------------
The cameras, as shown in the diagram, are supposed to be connected to VLAN 1 (I guess) where Internet access, as well as communication between other devices on the router or the managed switch, should be blocked.
The HikVision camera should be connected to a PoE switch and then to VLAN 1 of the managed switch.
The (outdoor) Wi-Fi Relolink camera should be connected wirelessly to either a TP-link extender or router, and from there to VLAN 1 using ethernet cable (not sure if this is the proper way though).
The PC running the custom CCTV server should be connected to VLAN 2, which will be provided Internet access, as well as access to VLAN 1 (so that the PC can access the video feed from the cameras), but no communication with other devices on the switch or the router should be allowed (I guess).
To remotely view the cameras, one should connect to the VPN server (using the WireGuard app, I guess) and access a simple local HTML page running on the PC server that provides the HLS or RTMP camera streams (converted from RTSP, using ffmpeg). I've seen that WireGuard allows one to set the internet traffic to go through VPN only if you are accessing LAN IPs, which will be convenient and thus, avoid using the VPN when browsing the web for other purposes.
Questions
----------
(1) Is this approach feasible and the most secure way possible to connect and access the cameras remotely?
(2) How to prevent other devices connected on the router, either wireless or wired, from accessing the VLAN 1 OR VLAN 2 devices?
(3) When connecting remotely through VPN to the home network, how is my remote device suppose to access the VLAN 2 PC server (if it is supposed to be isolated from other devices on LAN)?
(4) Should the HLS or RTMP stream be protected by credentials and how, if so?
(5) Should the HLS or RTMP stream be encrypted and how, if so? I understand that VPN will encrypt the traffic regardless on the frontend when remotely viewing, but if a device on the LAN acts maliciously, I guess it might be able to get the video feed.
(6) Is using managed switch with VLANs the only way to isolate devices connected through ethernet cables, or one could do that on the router alone as well?
Given how untrustworthy and vulnerable CCTV cameras and NVRs might be today, I would like to avoid connecting them directly to the Internet. Thus, I would like to build a custom system and securely connect to it for remote viewing. As networking might not necessarily be my area of expertise, I would like to ask for advice as to the most secure way to have my CCTV system connected to LAN and accessible remotely.
After doing some research, I figured that I should use VLANs to isolate the CCTV cameras and deny Internet access to them. On top of that, I should replace my router with one that provides a VPN server (such as TP-Link Archer BE230 that provides WireGuard) that should be used to remotely connect to my LAN, and hence, access my cameras.
My CCTV system comprises of POE cameras connected to a Reolink NVR, but I am also planning on connecting some Wi-Fi camera (as there is no possible way to run a cable to the area I would like to install it) and a HikVision PoE camera as well. Below I have provided a diagram of how I think the devices should be connected; however, like I said, I am not the expert in this field and that's why I would like to kindly ask for an expert's advice.
Diagram Notes
----------------
The cameras, as shown in the diagram, are supposed to be connected to VLAN 1 (I guess) where Internet access, as well as communication between other devices on the router or the managed switch, should be blocked.
The HikVision camera should be connected to a PoE switch and then to VLAN 1 of the managed switch.
The (outdoor) Wi-Fi Relolink camera should be connected wirelessly to either a TP-link extender or router, and from there to VLAN 1 using ethernet cable (not sure if this is the proper way though).
The PC running the custom CCTV server should be connected to VLAN 2, which will be provided Internet access, as well as access to VLAN 1 (so that the PC can access the video feed from the cameras), but no communication with other devices on the switch or the router should be allowed (I guess).
To remotely view the cameras, one should connect to the VPN server (using the WireGuard app, I guess) and access a simple local HTML page running on the PC server that provides the HLS or RTMP camera streams (converted from RTSP, using ffmpeg). I've seen that WireGuard allows one to set the internet traffic to go through VPN only if you are accessing LAN IPs, which will be convenient and thus, avoid using the VPN when browsing the web for other purposes.
Questions
----------
(1) Is this approach feasible and the most secure way possible to connect and access the cameras remotely?
(2) How to prevent other devices connected on the router, either wireless or wired, from accessing the VLAN 1 OR VLAN 2 devices?
(3) When connecting remotely through VPN to the home network, how is my remote device suppose to access the VLAN 2 PC server (if it is supposed to be isolated from other devices on LAN)?
(4) Should the HLS or RTMP stream be protected by credentials and how, if so?
(5) Should the HLS or RTMP stream be encrypted and how, if so? I understand that VPN will encrypt the traffic regardless on the frontend when remotely viewing, but if a device on the LAN acts maliciously, I guess it might be able to get the video feed.
(6) Is using managed switch with VLANs the only way to isolate devices connected through ethernet cables, or one could do that on the router alone as well?

