Hello aster1x - I don't mean to confuse, apologies. But I do admit that I like tinkering around with these things, so what I did on my setup may not be suitable or useful to all. But hey, it works OK for me, as my NVR is on top of some wall cupboards in a utility room on the end of a gigabit cable connection, with 5 cameras directly wired to the PoE ports. I didn't want to add another gigabit switch just to connect the normal LAN to a PoE port.
So - to clarify and answer:
The normal LAN is as you indicate 192.168.1.xxx, default router / gateway = 192.168.1.1
Hikvision NVR model 7816N-E2/8P IP address=192.168.1.210 Firmware = 3.0.8
The NVR PoE network interface = 192.168.254.1, PoE ports can be in the range 192.168.254.2-xxx
Here is a key item - the LAN router has a static route defined - for the 192.168.254.0 255.255.255.0 network, the gateway address = the LAN IP of the NVR, ie 192.168.1.210
This means that any device on the LAN is informed to route traffic for the NVR PoE ports to the NVR at 192.168.1.210
The QNAP NAS being a Linux box gets the route then just connects directly to the NVR LAN address to communicate with the PoE connected cameras.
How does the routing between LAN and PoE ports work? It's done in the NVR Linux kernel, which having 2 Ethernet interfaces, has the facility to do 'ip_forwarding' between the 2 interfaces.
On my NVR, this is disabled by default on bootup. I don't have Virtual Host. I suspect that on NVRs with Virtual Host, it will be enabled by default.
As it probably is on cigar7's NVR, I'd bet there is a network loop when two cables are connected from the NVR.
The method I used for my, admittedly slightly unusual, setup is described here: As I said - not for all ...
http://www.ipcamtalk.com/showthread...-cameras-without-virtual-host-or-extra-wiring
I would be surprised if your 76xx /xP could not also do the IP routing between the 2 interfaces. With some care - check out the /proc/sys/net/ipv4/ip_forward value, turn it on and off with 1 or 0 respectively, and test the access. But remember you need the static route, manual config on PoE ports and cameras, and a web port other than 80 on the cameras.
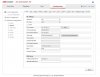
I don't use email alerts - would get far too many with outside cameras - but here is a screenshot of a camera on a PoE port accessing the internet for its NTP value: