Hi guys,
I'm having some fun with a hardware/software analysis of the Dahua DHI-ASI7213X-T1 thermal camera and I have some questions for you:
HARDWARE:
- Anyone can explain me why there is a stm32f103c8 in the back side of the PCB?
SOFTWARE
I tried to decompress the firmware (DahuaWiki) using both binwalk and the tools posted in this forum some years ago (GitHub - BotoX/Dahua-Firmware-Mod-Kit: Unpack and repack Dahua IP camera firmware upgrade images.). From those tools, I succeeded only in getting the u-boot.bin file in a correct way, the other sections of the firmware are not decompressed correctly.
Here are some screenshots of the binwalk result, together with the list of obtained files.

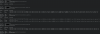
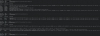
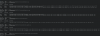
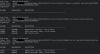
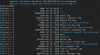
For what concerns dhboot (actually it is uboot) there are no problems, it is correctly extranted.
I tried to use unsquashfs and sasquatch to read the content of those files with squashfs but without any good results.
Binwalk produce two .gz files in the _firmware-x.squashfs.img.extracted folder, but the common unzip tools are not able to open those files.
The _partition-x.cramfs.img.extracted contains empty files.
I noticed that the u-boot contains a AES Inverse-SBOX; are there any encrypted sections?
Can someone help me in figuring out how to correctly read those files?
Thank you!
I'm having some fun with a hardware/software analysis of the Dahua DHI-ASI7213X-T1 thermal camera and I have some questions for you:
HARDWARE:
- Anyone can explain me why there is a stm32f103c8 in the back side of the PCB?
SOFTWARE
I tried to decompress the firmware (DahuaWiki) using both binwalk and the tools posted in this forum some years ago (GitHub - BotoX/Dahua-Firmware-Mod-Kit: Unpack and repack Dahua IP camera firmware upgrade images.). From those tools, I succeeded only in getting the u-boot.bin file in a correct way, the other sections of the firmware are not decompressed correctly.
Here are some screenshots of the binwalk result, together with the list of obtained files.


For what concerns dhboot (actually it is uboot) there are no problems, it is correctly extranted.
I tried to use unsquashfs and sasquatch to read the content of those files with squashfs but without any good results.
Binwalk produce two .gz files in the _firmware-x.squashfs.img.extracted folder, but the common unzip tools are not able to open those files.
The _partition-x.cramfs.img.extracted contains empty files.
I noticed that the u-boot contains a AES Inverse-SBOX; are there any encrypted sections?
Can someone help me in figuring out how to correctly read those files?
Thank you!
