Bios flashing hikvision
- Thread starter Sparktikus
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
alastairstevenson
Staff member
You need to dig a little deeper and connect to the serial console to see if there is any low-level activity that may help to diagnose and repair the problem.Not booting, no bios, nothing on display - totally blank
To connect to the serial console, you'll need these 2 items or similar :
A 4-pin 1.5mm JST ZH wired connector, usually sold in 10-packs.
A USB to TTL serial adaptor, such as a PL2303TA-based device.
Both widely available on eBay at low prices.
I would have just flashed the bios if had required files
I have the equipment needed to connect to serial console
But what low level activity would I be looking for?
how would this help?
Thanks
I have the equipment needed to connect to serial console
But what low level activity would I be looking for?
how would this help?
Thanks
alastairstevenson
Staff member
The system startup log if it exists, and the detail of how far the bootup sequence progresses.But what low level activity would I be looking for?
how would this help?
It may just need a firmware reflash, or it may show there there is a hardware fault.
Generally, the system log provides a lot of information and is easy to connect to.
mohammadgharib
n3wb
can we change mac address of hikvision IP camera with this solution because I reprogram 2 hikvision IP camera and now both of them have the same Mac address. and I can't use them in a same home networkThe system startup log if it exists, and the detail of how far the bootup sequence progresses.
It may just need a firmware reflash, or it may show there there is a hardware fault.
Generally, the system log provides a lot of information and is easy to connect to.
alastairstevenson
Staff member
How did you do this?I reprogram 2 hikvision IP camera and now both of them have the same Mac address
By writing the flash chip with a programmer?
Depending on the model and firmware version of the (unspecified) cameras, the MAC address is held in a protected area.
An answer needs more detail in the question.
mohammadgharib
n3wb
yes I had 2cd2032f-i models and flash chip bios 48pins Toshiba with programmer and it makes them to have same MAC address but I want to change the MAC address to use them in same home network. I will attach the file that I use if neededHow did you do this?
By writing the flash chip with a programmer?
Depending on the model and firmware version of the (unspecified) cameras, the MAC address is held in a protected area.
An answer needs more detail in the question.
alastairstevenson
Staff member
You are in luck then - the MAC address is held in plain form in a known location in the flash memory of that model.I had 2cd2032f-i models and flash chip
Here is the flash layout :
Code:
0.541255] Creating 18 MTD partitions on "ambnand":
[ 0.541293] 0x000000000000-0x000000020000 : "bst"
[ 0.545520] 0x000000020000-0x000000120000 : "ptb"
[ 0.549293] 0x000000120000-0x000000220000 : "bld"
[ 0.553387] 0x000000220000-0x000000320000 : "hal"
[ 0.557298] 0x000000320000-0x000000420000 : "ano_ptb"
[ 0.561228] 0x000000420000-0x0000004a0000 : "env"
[ 0.565529] 0x0000004a0000-0x000000520000 : "param"
[ 0.569565] 0x000000520000-0x000000620000 : "dpt"
[ 0.573912] 0x000000620000-0x000001020000 : "rcvy"
[ 0.578136] 0x000001020000-0x000001820000 : "krn_pri"
[ 0.582052] 0x000001820000-0x000002020000 : "krn_sec"
[ 0.586281] 0x000002020000-0x000002420000 : "rmd_pri"
[ 0.590281] 0x000002420000-0x000002820000 : "rmd_sec"
[ 0.594607] 0x000002820000-0x000004020000 : "app_pri"
[ 0.598739] 0x000004020000-0x000005820000 : "app_sec"
[ 0.603201] 0x000005820000-0x000005c20000 : "cfg_pri"
[ 0.607370] 0x000005c20000-0x000006020000 : "cfg_sec"
[ 0.611679] 0x000006020000-0x000007020000 : "dbg"The 'bootparams' holding MAC address and other info is in mtdblock6 at this offset in the 'param' segment :
0x0000004a0000-0x000000520000 : "param"
The MAC address is the 6 bytes at location 0x35 in that flash segment.
Just change one byte or bit and re-flash with the modified file.
Here is the data to look for starting at 0x4a0000
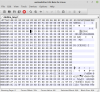
mohammadgharib
n3wb
thanks for your information I used the hex editor but in decode box I got some weird notes. as you can see in picture. how can i use them?You are in luck then - the MAC address is held in plain form in a known location in the flash memory of that model.
Here is the flash layout :
Code:0.541255] Creating 18 MTD partitions on "ambnand": [ 0.541293] 0x000000000000-0x000000020000 : "bst" [ 0.545520] 0x000000020000-0x000000120000 : "ptb" [ 0.549293] 0x000000120000-0x000000220000 : "bld" [ 0.553387] 0x000000220000-0x000000320000 : "hal" [ 0.557298] 0x000000320000-0x000000420000 : "ano_ptb" [ 0.561228] 0x000000420000-0x0000004a0000 : "env" [ 0.565529] 0x0000004a0000-0x000000520000 : "param" [ 0.569565] 0x000000520000-0x000000620000 : "dpt" [ 0.573912] 0x000000620000-0x000001020000 : "rcvy" [ 0.578136] 0x000001020000-0x000001820000 : "krn_pri" [ 0.582052] 0x000001820000-0x000002020000 : "krn_sec" [ 0.586281] 0x000002020000-0x000002420000 : "rmd_pri" [ 0.590281] 0x000002420000-0x000002820000 : "rmd_sec" [ 0.594607] 0x000002820000-0x000004020000 : "app_pri" [ 0.598739] 0x000004020000-0x000005820000 : "app_sec" [ 0.603201] 0x000005820000-0x000005c20000 : "cfg_pri" [ 0.607370] 0x000005c20000-0x000006020000 : "cfg_sec" [ 0.611679] 0x000006020000-0x000007020000 : "dbg"
The 'bootparams' holding MAC address and other info is in mtdblock6 at this offset in the 'param' segment :
0x0000004a0000-0x000000520000 : "param"
The MAC address is the 6 bytes at location 0x35 in that flash segment.
Just change one byte or bit and re-flash with the modified file.
Here is the data to look for starting at 0x4a0000
View attachment 110001
edit:now I see everything except how can I find the part about Mac Address to change it
Attachments
Last edited:
alastairstevenson
Staff member
That's not what I'd expect to see in mtdblock6 from a DS-2CD2032I used the hex editor but in decode box I got some weird notes.
What version of firmware is in it?
I'm not sure if this means the data looks like my example.edit:now I see everything except how can I find the part about Mac Address to change it
mohammadgharib
n3wb
I found something similar. this is all of ic flash it is a bin file with so much dataThat's not what I'd expect to see in mtdblock6 from a DS-2CD2032
What version of firmware is in it?
I'm not sure if this means the data looks like my example.
Attachments
alastairstevenson
Staff member
That certainly looks like the right data.I found something similar.
But that's in the 'env' partition, mtdblock5 which as far as I know does not get used.
In total, there are normally 4 instances of that block, one in mtdblock5 and 3 in mtdblock6, but the location that I highlighted is the active one.
It looks like the block in your original screenshot may be encrypted. Or corrupted.
I've not seen that in the R0 series (DS-2CD2032) cameras, but I had not checked that in the newest firmware.
I just checked an mtdblock6 from a DS-2CD2032 with firmware V5.4.5 build 170123 and the block is still in plain form.
mohammadgharib
n3wb
sorry not to mention: this camera is not the R0 series. it is English version and it has IC chip .bin program and I'm sending it in the LINK Download . please take a look at it and tell me which part of this is the right one for 'env' partitionThat certainly looks like the right data.
But that's in the 'env' partition, mtdblock5 which as far as I know does not get used.
In total, there are normally 4 instances of that block, one in mtdblock5 and 3 in mtdblock6, but the location that I highlighted is the active one.
It looks like the block in your original screenshot may be encrypted. Or corrupted.
I've not seen that in the R0 series (DS-2CD2032) cameras, but I had not checked that in the newest firmware.
I just checked an mtdblock6 from a DS-2CD2032 with firmware V5.4.5 build 170123 and the block is still in plain form.
mohammadgharib
n3wb
update: after more reading about R0 series and... I think I know what is mtdblock6 but my problem is can I extract this mtdblock6 from model DS-2CD1031-I and change its MAC Address?
and also the model DS-2CD2032F-I is still my problem. as I told you I just reprogram IC FLash with the .bin file which I sent you above and now I have 3 different cameras with same model which is 2032 and also same Mac address. These are English version Cameras. and now with same Mac Address I can't use them in a same Network.
and also the model DS-2CD2032F-I is still my problem. as I told you I just reprogram IC FLash with the .bin file which I sent you above and now I have 3 different cameras with same model which is 2032 and also same Mac address. These are English version Cameras. and now with same Mac Address I can't use them in a same Network.
alastairstevenson
Staff member
I have looked at the flash dump that you linked to.the model DS-2CD2032F-I is still my problem. as I told you I just reprogram IC FLash with the .bin file which I sent you above and now I have 3 different cameras with same model which is 2032 and also same Mac address.
It is similar, but is not an exact match, to the many DS-2CD2032 cameras I've looked at - the partition boundaries are in different locations.
Also - the flash dump appears to be a composite of 2 different cameras of the same model but different serial numbers, running the 5.3.0 firmware that does not validate bootpara data against the block checksum.
However - it does have the normal 4 copies of the 'bootpara' data that holds the MAC address as well as other values set during manufacturing.
With the proviso that with those unknowns, there is some uncertainty in re-flashing a camera with it, attached is a modded version of the file you linked to, where the locations holding the MAC address have been changed by one bit.
If you feel able to take the risk - you could try re-flashing the camera with this modified version.
Presumably if there is a problem - you can re-flash with the copy that you originally extracted.
When you did the extract - did you do a verification of the extracted data against the original?
Alternatively, it should be possible to extract mtdblock6 and make changes to the stored MAC address but not the language byte (already set as English) and re-apply if you follow the brickfixV2 process here :
R0 / DS-2CD2x32 BrickfixV2 brick recovery and full upgrade tool - enhanced.
The original 'brick-fix tool' and 'enhanced mtd hack' has proven pretty useful for those with R0 cameras that had been bricked by doing a firmware update. It's been even more useful to deal with the fallout from the 'Hikvision backdoor' disclosure where so many people are finding their cameras...