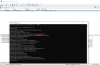
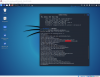
import socket
# Configuration
UDP_IP = "239.255.255.250" # Broadcast IP address
UDP_PORT = 202 # I need to remember which port it was, you can check what sadp is using
# Create UDP socket
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.setsockopt(socket.SOL_SOCKET, socket.SO_BROADCAST, 1)
# Send data as UDP broadcast packet
data = bytes([
0x3c, 0x3f, 0x78, 0x6d, 0x6c, 0x20, 0x76, 0x65,
0x72, 0x73, 0x69, 0x6f, 0x6e, 0x3d, 0x22, 0x31,
0x2e, 0x30, 0x22, 0x20, 0x65, 0x6e, 0x63, 0x6f,
0x64, 0x69, 0x6e, 0x67, 0x3d, 0x22, 0x55, 0x54,
0x46, 0x2d, 0x38, 0x22, 0x3f, 0x3e, 0x0d, 0x0a,
0x3c, 0x50, 0x72, 0x6f, 0x62, 0x65, 0x4d, 0x61,
0x74, 0x63, 0x68, 0x3e, 0x3c, 0x55, 0x75, 0x69,
0x64, 0x3e, 0x37, 0x31, 0x39, 0x44, 0x38, 0x32,
0x45, 0x41, 0x2d, 0x36, 0x33, 0x36, 0x46, 0x2d,
0x34, 0x44, 0x35, 0x35, 0x2d, 0x42, 0x39, 0x41,
0x30, 0x2d, 0x30, 0x43, 0x33, 0x38, 0x39, 0x37,
0x33, 0x34, 0x43, 0x36, 0x38, 0x44, 0x3c, 0x2f,
0x55, 0x75, 0x69, 0x64, 0x3e, 0x0d, 0x0a, 0x3c,
0x54, 0x79, 0x70, 0x65, 0x73, 0x3e, 0x69, 0x6e,
0x71, 0x75, 0x69, 0x72, 0x79, 0x3c, 0x2f, 0x54,
0x79, 0x70, 0x65, 0x73, 0x3e, 0x0d, 0x0a, 0x3c,
0x44, 0x65, 0x76, 0x69, 0x63, 0x65, 0x54, 0x79,
0x70, 0x65, 0x3e, 0x31, 0x34, 0x30, 0x36, 0x38,
0x38, 0x3c, 0x2f, 0x44, 0x65, 0x76, 0x69, 0x63,
0x65, 0x54, 0x79, 0x70, 0x65, 0x3e, 0x0d, 0x0a,
0x3c, 0x44, 0x65, 0x76, 0x69, 0x63, 0x65, 0x44,
0x65, 0x73, 0x63, 0x72, 0x69, 0x70, 0x74, 0x69,
0x6f, 0x6e, 0x3e, 0x44, 0x53, 0x2d, 0x32, 0x43,
0x44, 0x31, 0x33, 0x34, 0x33, 0x47, 0x30, 0x2d,
0x49, 0x3c, 0x2f, 0x44, 0x65, 0x76, 0x69, 0x63,
0x65, 0x44, 0x65, 0x73, 0x63, 0x72, 0x69, 0x70,
0x74, 0x69, 0x6f, 0x6e, 0x3e, 0x0d, 0x0a, 0x3c,
0x44, 0x65, 0x76, 0x69, 0x63, 0x65, 0x53, 0x4e,
0x3e, 0x44, 0x53, 0x2d, 0x32, 0x43, 0x44, 0x31,
0x33, 0x34, 0x33, 0x47, 0x30, 0x2d, 0x49, 0x32,
0x30, 0x31, 0x39, 0x31, 0x32, 0x32, 0x32, 0x41,
0x41, 0x57, 0x52, 0x45, 0x30, 0x34, 0x34, 0x36,
0x38, 0x31, 0x37, 0x34, 0x3c, 0x2f, 0x44, 0x65,
0x76, 0x69, 0x63, 0x65, 0x53, 0x4e, 0x3e, 0x0d,
0x0a, 0x3c, 0x43, 0x6f, 0x6d, 0x6d, 0x61, 0x6e,
0x64, 0x50, 0x6f, 0x72, 0x74, 0x3e, 0x38, 0x30,
0x30, 0x30, 0x3c, 0x2f, 0x43, 0x6f, 0x6d, 0x6d,
0x61, 0x6e, 0x64, 0x50, 0x6f, 0x72, 0x74, 0x3e,
0x0d, 0x0a, 0x3c, 0x48, 0x74, 0x74, 0x70, 0x50,
0x6f, 0x72, 0x74, 0x3e, 0x38, 0x30, 0x3c, 0x2f,
0x48, 0x74, 0x74, 0x70, 0x50, 0x6f, 0x72, 0x74,
0x3e, 0x0d, 0x0a, 0x3c, 0x4d, 0x41, 0x43, 0x3e,
0x39, 0x38, 0x2d, 0x64, 0x66, 0x2d, 0x38, 0x32,
0x2d, 0x36, 0x62, 0x2d, 0x31, 0x62, 0x2d, 0x33,
0x62, 0x3c, 0x2f, 0x4d, 0x41, 0x43, 0x3e, 0x0d,
0x0a, 0x3c, 0x49, 0x50, 0x76, 0x34, 0x41, 0x64,
0x64, 0x72, 0x65, 0x73, 0x73, 0x3e, 0x31, 0x39,
0x32, 0x2e, 0x31, 0x36, 0x38, 0x2e, 0x31, 0x38,
0x2e, 0x32, 0x30, 0x32, 0x3c, 0x2f, 0x49, 0x50,
0x76, 0x34, 0x41, 0x64, 0x64, 0x72, 0x65, 0x73,
0x73, 0x3e, 0x0d, 0x0a, 0x3c, 0x49, 0x50, 0x76,
0x34, 0x53, 0x75, 0x62, 0x6e, 0x65, 0x74, 0x4d,
0x61, 0x73, 0x6b, 0x3e, 0x32, 0x35, 0x35, 0x2e,
0x32, 0x35, 0x35, 0x2e, 0x32, 0x35, 0x32, 0x2e,
0x30, 0x3c, 0x2f, 0x49, 0x50, 0x76, 0x34, 0x53,
0x75, 0x62, 0x6e, 0x65, 0x74, 0x4d, 0x61, 0x73,
0x6b, 0x3e, 0x0d, 0x0a, 0x3c, 0x49, 0x50, 0x76,
0x34, 0x47, 0x61, 0x74, 0x65, 0x77, 0x61, 0x79,
0x3e, 0x31, 0x39, 0x32, 0x2e, 0x31, 0x36, 0x38,
0x2e, 0x31, 0x36, 0x2e, 0x37, 0x3c, 0x2f, 0x49,
0x50, 0x76, 0x34, 0x47, 0x61, 0x74, 0x65, 0x77,
0x61, 0x79, 0x3e, 0x0d, 0x0a, 0x3c, 0x49, 0x50,
0x76, 0x36, 0x41, 0x64, 0x64, 0x72, 0x65, 0x73,
0x73, 0x3e, 0x3a, 0x3a, 0x3c, 0x2f, 0x49, 0x50,
0x76, 0x36, 0x41, 0x64, 0x64, 0x72, 0x65, 0x73,
0x73, 0x3e, 0x0d, 0x0a, 0x3c, 0x49, 0x50, 0x76,
0x36, 0x47, 0x61, 0x74, 0x65, 0x77, 0x61, 0x79,
0x3e, 0x3a, 0x3a, 0x3c, 0x2f, 0x49, 0x50, 0x76,
0x36, 0x47, 0x61, 0x74, 0x65, 0x77, 0x61, 0x79,
0x3e, 0x0d, 0x0a, 0x3c, 0x49, 0x50, 0x76, 0x36,
0x4d, 0x61, 0x73, 0x6b, 0x4c, 0x65, 0x6e, 0x3e,
0x36, 0x34, 0x3c, 0x2f, 0x49, 0x50, 0x76, 0x36,
0x4d, 0x61, 0x73, 0x6b, 0x4c, 0x65, 0x6e, 0x3e,
0x0d, 0x0a, 0x3c, 0x44, 0x48, 0x43, 0x50, 0x3e,
0x74, 0x72, 0x75, 0x65, 0x3c, 0x2f, 0x44, 0x48,
0x43, 0x50, 0x3e, 0x0d, 0x0a, 0x3c, 0x41, 0x6e,
0x61, 0x6c, 0x6f, 0x67, 0x43, 0x68, 0x61, 0x6e,
0x6e, 0x65, 0x6c, 0x4e, 0x75, 0x6d, 0x3e, 0x30,
0x3c, 0x2f, 0x41, 0x6e, 0x61, 0x6c, 0x6f, 0x67,
0x43, 0x68, 0x61, 0x6e, 0x6e, 0x65, 0x6c, 0x4e,
0x75, 0x6d, 0x3e, 0x0d, 0x0a, 0x3c, 0x44, 0x69,
0x67, 0x69, 0x74, 0x61, 0x6c, 0x43, 0x68, 0x61,
0x6e, 0x6e, 0x65, 0x6c, 0x4e, 0x75, 0x6d, 0x3e,
0x31, 0x3c, 0x2f, 0x44, 0x69, 0x67, 0x69, 0x74,
0x61, 0x6c, 0x43, 0x68, 0x61, 0x6e, 0x6e, 0x65,
0x6c, 0x4e, 0x75, 0x6d, 0x3e, 0x0d, 0x0a, 0x3c,
0x53, 0x6f, 0x66, 0x74, 0x77, 0x61, 0x72, 0x65,
0x56, 0x65, 0x72, 0x73, 0x69, 0x6f, 0x6e, 0x3e,
0x56, 0x35, 0x2e, 0x35, 0x2e, 0x38, 0x39, 0x62,
0x75, 0x69, 0x6c, 0x64, 0x20, 0x32, 0x31, 0x30,
0x34, 0x32, 0x39, 0x3c, 0x2f, 0x53, 0x6f, 0x66,
0x74, 0x77, 0x61, 0x72, 0x65, 0x56, 0x65, 0x72,
0x73, 0x69, 0x6f, 0x6e, 0x3e, 0x0d, 0x0a, 0x3c,
0x44, 0x53, 0x50, 0x56, 0x65, 0x72, 0x73, 0x69,
0x6f, 0x6e, 0x3e, 0x56, 0x37, 0x2e, 0x33, 0x20,
0x62, 0x75, 0x69, 0x6c, 0x64, 0x20, 0x32, 0x31,
0x30, 0x32, 0x30, 0x37, 0x3c, 0x2f, 0x44, 0x53,
0x50, 0x56, 0x65, 0x72, 0x73, 0x69, 0x6f, 0x6e,
0x3e, 0x0d, 0x0a, 0x3c, 0x42, 0x6f, 0x6f, 0x74,
0x54, 0x69, 0x6d, 0x65, 0x3e, 0x32, 0x30, 0x32,
0x33, 0x2d, 0x30, 0x31, 0x2d, 0x31, 0x37, 0x20,
0x30, 0x37, 0x3a, 0x34, 0x36, 0x3a, 0x32, 0x34,
0x3c, 0x2f, 0x42, 0x6f, 0x6f, 0x74, 0x54, 0x69,
0x6d, 0x65, 0x3e, 0x0d, 0x0a, 0x3c, 0x45, 0x6e,
0x63, 0x72, 0x79, 0x70, 0x74, 0x3e, 0x74, 0x72,
0x75, 0x65, 0x3c, 0x2f, 0x45, 0x6e, 0x63, 0x72,
0x79, 0x70, 0x74, 0x3e, 0x0d, 0x0a, 0x3c, 0x52,
0x65, 0x73, 0x65, 0x74, 0x41, 0x62, 0x69, 0x6c,
0x69, 0x74, 0x79, 0x3e, 0x66, 0x61, 0x6c, 0x73,
0x65, 0x3c, 0x2f, 0x52, 0x65, 0x73, 0x65, 0x74,
0x41, 0x62, 0x69, 0x6c, 0x69, 0x74, 0x79, 0x3e,
0x0d, 0x0a, 0x3c, 0x44, 0x69, 0x73, 0x6b, 0x4e,
0x75, 0x6d, 0x62, 0x65, 0x72, 0x3e, 0x30, 0x3c,
0x2f, 0x44, 0x69, 0x73, 0x6b, 0x4e, 0x75, 0x6d,
0x62, 0x65, 0x72, 0x3e, 0x0d, 0x0a, 0x3c, 0x41,
0x63, 0x74, 0x69, 0x76, 0x61, 0x74, 0x65, 0x64,
0x3e, 0x74, 0x72, 0x75, 0x65, 0x3c, 0x2f, 0x41,
0x63, 0x74, 0x69, 0x76, 0x61, 0x74, 0x65, 0x64,
0x3e, 0x0d, 0x0a, 0x3c, 0x50, 0x61, 0x73, 0x73,
0x77, 0x6f, 0x72, 0x64, 0x52, 0x65, 0x73, 0x65,
0x74, 0x41, 0x62, 0x69, 0x6c, 0x69, 0x74, 0x79,
0x3e, 0x74, 0x72, 0x75, 0x65, 0x3c, 0x2f, 0x50,
0x61, 0x73, 0x73, 0x77, 0x6f, 0x72, 0x64, 0x52,
0x65, 0x73, 0x65, 0x74, 0x41, 0x62, 0x69, 0x6c,
0x69, 0x74, 0x79, 0x3e, 0x0d, 0x0a, 0x3c, 0x50,
0x61, 0x73, 0x73, 0x77, 0x6f, 0x72, 0x64, 0x52,
0x65, 0x73, 0x65, 0x74, 0x4d, 0x6f, 0x64, 0x65,
0x53, 0x65, 0x63, 0x6f, 0x6e, 0x64, 0x3e, 0x74,
0x72, 0x75, 0x65, 0x3c, 0x2f, 0x50, 0x61, 0x73,
0x73, 0x77, 0x6f, 0x72, 0x64, 0x52, 0x65, 0x73,
0x65, 0x74, 0x4d, 0x6f, 0x64, 0x65, 0x53, 0x65,
0x63, 0x6f, 0x6e, 0x64, 0x3e, 0x0d, 0x0a, 0x3c,
0x44, 0x65, 0x74, 0x61, 0x69, 0x6c, 0x4f, 0x45,
0x4d, 0x43, 0x6f, 0x64, 0x65, 0x3e, 0x31, 0x3c,
0x2f, 0x44, 0x65, 0x74, 0x61, 0x69, 0x6c, 0x4f,
0x45, 0x4d, 0x43, 0x6f, 0x64, 0x65, 0x3e, 0x0d,
0x0a, 0x3c, 0x53, 0x75, 0x70, 0x70, 0x6f, 0x72,
0x74, 0x53, 0x65, 0x63, 0x75, 0x72, 0x69, 0x74,
0x79, 0x51, 0x75, 0x65, 0x73, 0x74, 0x69, 0x6f,
0x6e, 0x3e, 0x74, 0x72, 0x75, 0x65, 0x3c, 0x2f,
0x53, 0x75, 0x70, 0x70, 0x6f, 0x72, 0x74, 0x53,
0x65, 0x63, 0x75, 0x72, 0x69, 0x74, 0x79, 0x51,
0x75, 0x65, 0x73, 0x74, 0x69, 0x6f, 0x6e, 0x3e,
0x0d, 0x0a, 0x3c, 0x53, 0x75, 0x70, 0x70, 0x6f,
0x72, 0x74, 0x48, 0x43, 0x50, 0x6c, 0x61, 0x74,
0x66, 0x6f, 0x72, 0x6d, 0x3e, 0x74, 0x72, 0x75,
0x65, 0x3c, 0x2f, 0x53, 0x75, 0x70, 0x70, 0x6f,
0x72, 0x74, 0x48, 0x43, 0x50, 0x6c, 0x61, 0x74,
0x66, 0x6f, 0x72, 0x6d, 0x3e, 0x0d, 0x0a, 0x3c,
0x48, 0x43, 0x50, 0x6c, 0x61, 0x74, 0x66, 0x6f,
0x72, 0x6d, 0x45, 0x6e, 0x61, 0x62, 0x6c, 0x65,
0x3e, 0x74, 0x72, 0x75, 0x65, 0x3c, 0x2f, 0x48,
0x43, 0x50, 0x6c, 0x61, 0x74, 0x66, 0x6f, 0x72,
0x6d, 0x45, 0x6e, 0x61, 0x62, 0x6c, 0x65, 0x3e,
0x0d, 0x0a, 0x3c, 0x49, 0x73, 0x4d, 0x6f, 0x64,
0x69, 0x66, 0x79, 0x56, 0x65, 0x72, 0x69, 0x66,
0x69, 0x63, 0x61, 0x74, 0x69, 0x6f, 0x6e, 0x43,
0x6f, 0x64, 0x65, 0x3e, 0x66, 0x6c, 0x61, 0x73,
0x65, 0x3c, 0x2f, 0x49, 0x73, 0x4d, 0x6f, 0x64,
0x69, 0x66, 0x79, 0x56, 0x65, 0x72, 0x69, 0x66,
0x69, 0x63, 0x61, 0x74, 0x69, 0x6f, 0x6e, 0x43,
0x6f, 0x64, 0x65, 0x3e, 0x0d, 0x0a, 0x3c, 0x53,
0x61, 0x6c, 0x74, 0x3e, 0x32, 0x30, 0x64, 0x66,
0x36, 0x62, 0x31, 0x33, 0x66, 0x36, 0x62, 0x38,
0x34, 0x62, 0x30, 0x30, 0x63, 0x33, 0x63, 0x31,
0x66, 0x32, 0x34, 0x61, 0x33, 0x32, 0x64, 0x63,
0x33, 0x36, 0x62, 0x36, 0x66, 0x30, 0x36, 0x66,
0x37, 0x34, 0x35, 0x37, 0x36, 0x63, 0x63, 0x61,
0x35, 0x39, 0x64, 0x31, 0x66, 0x33, 0x33, 0x62,
0x36, 0x36, 0x39, 0x65, 0x38, 0x32, 0x30, 0x35,
0x34, 0x31, 0x61, 0x35, 0x3c, 0x2f, 0x53, 0x61,
0x6c, 0x74, 0x3e, 0x0d, 0x0a, 0x3c, 0x44, 0x65,
0x76, 0x69, 0x63, 0x65, 0x4c, 0x6f, 0x63, 0x6b,
0x3e, 0x74, 0x72, 0x75, 0x65, 0x3c, 0x2f, 0x44,
0x65, 0x76, 0x69, 0x63, 0x65, 0x4c, 0x6f, 0x63,
0x6b, 0x3e, 0x0d, 0x0a, 0x3c, 0x53, 0x44, 0x4b,
0x53, 0x65, 0x72, 0x76, 0x65, 0x72, 0x53, 0x74,
0x61, 0x74, 0x75, 0x73, 0x3e, 0x74, 0x72, 0x75,
0x65, 0x3c, 0x2f, 0x53, 0x44, 0x4b, 0x53, 0x65,
0x72, 0x76, 0x65, 0x72, 0x53, 0x74, 0x61, 0x74,
0x75, 0x73, 0x3e, 0x0d, 0x0a, 0x3c, 0x53, 0x44,
0x4b, 0x4f, 0x76, 0x65, 0x72, 0x54, 0x4c, 0x53,
0x53, 0x65, 0x72, 0x76, 0x65, 0x72, 0x53, 0x74,
0x61, 0x74, 0x75, 0x73, 0x3e, 0x74, 0x72, 0x75,
0x65, 0x3c, 0x2f, 0x53, 0x44, 0x4b, 0x4f, 0x76,
0x65, 0x72, 0x54, 0x4c, 0x53, 0x53, 0x65, 0x72,
0x76, 0x65, 0x72, 0x53, 0x74, 0x61, 0x74, 0x75,
0x73, 0x3e, 0x0d, 0x0a, 0x3c, 0x53, 0x44, 0x4b,
0x4f, 0x76, 0x65, 0x72, 0x54, 0x4c, 0x53, 0x50,
0x6f, 0x72, 0x74, 0x3e, 0x38, 0x34, 0x34, 0x33,
0x3c, 0x2f, 0x53, 0x44, 0x4b, 0x4f, 0x76, 0x65,
0x72, 0x54, 0x4c, 0x53, 0x50, 0x6f, 0x72, 0x74,
0x3e, 0x0d, 0x0a, 0x3c, 0x53, 0x75, 0x70, 0x70,
0x6f, 0x72, 0x74, 0x4d, 0x61, 0x69, 0x6c, 0x42,
0x6f, 0x78, 0x3e, 0x74, 0x72, 0x75, 0x65, 0x3c,
0x2f, 0x53, 0x75, 0x70, 0x70, 0x6f, 0x72, 0x74,
0x4d, 0x61, 0x69, 0x6c, 0x42, 0x6f, 0x78, 0x3e,
0x0d, 0x0a, 0x3c, 0x73, 0x75, 0x70, 0x70, 0x6f,
0x72, 0x74, 0x45, 0x7a, 0x76, 0x69, 0x7a, 0x55,
0x6e, 0x62, 0x69, 0x6e, 0x64, 0x3e, 0x74, 0x72,
0x75, 0x65, 0x3c, 0x2f, 0x73, 0x75, 0x70, 0x70,
0x6f, 0x72, 0x74, 0x45, 0x7a, 0x76, 0x69, 0x7a,
0x55, 0x6e, 0x62, 0x69, 0x6e, 0x64, 0x3e, 0x0d,
0x0a, 0x3c, 0x2f, 0x50, 0x72, 0x6f, 0x62, 0x65,
0x4d, 0x61, 0x74, 0x63, 0x68, 0x3e, 0x0d, 0x0a]) # Will send byte array later, or take from wireshark aswell as port for broadcast packet
sock.sendto(data, (UDP_IP, UDP_PORT))
print("Sent UDP broadcast packet.")
# Receive response from devices
sock.bind(("0.0.0.0", UDP_PORT))
print("Listening for responses...")
while True:
response, addr = sock.recvfrom(1024)
print("Received response from {}: {}".format(addr[0], response.decode()))