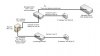
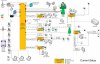
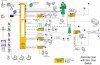
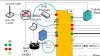
Based on that diagram,
Blue Iris would see the two cameras but presumably not see the internet (if your router is not part of Vlan 20).
Using a different subnet mask is not necessary.
To really understand the purpose of the subnet mask, I think it helps to see things in raw binary form. Your computer has a network interface with the address
192.168.0.50. In raw binary, it looks like this:
Code:
11000000.10101000.00000000.00110010
So there you see your address is 32 "bits" long. I added a dot after every 8 bits for readability, so the dots appear in the same place as when you write out the address as
192.168.0.50.
Then comes the subnet mask. The subnet mask essentially tells the computer how big the network is.
255.255.255.0 is the most common subnet mask, which, converted to binary, is:
Code:
11111111.11111111.11111111.00000000
Note how each 8-bit section is all 1s or 0s. This is easy for us humans to intuitively understand and remember, which is why this is such a common subnet mask.
What this mask means is that the first 24 bits (3 full bytes) of the IP address define the network the machine is on, and the last 8 bits (1 full byte) is the machine's address on the network.
In other words, because of that subnet mask, we know that
192.168.0 defines the network, and
50 defines the machine's address on the network. The first and last addresses on the network (
192.168.0.0 and
192.168.0.255) are always reserved for special purposes, which means all the addresses in between (
192.168.0.1 to
192.168.0.254) are free to be assigned to devices.
When you use a second NIC and assign it the address
192.168.20.51 with subnet mask
255.255.255.0, that just means the network is
192.168.20 and the machine's address on that network is
51, and the usable addresses range from
192.168.20.1 to
192.168.20.254. This does not overlap with your first network, so you're all good.
If you wanted to make things painful, you could use a different subnet mask where the transition from 1s to 0s does not align with the byte boundaries such as
255.255.255.128, which in binary is:
Code:
11111111.11111111.11111111.10000000
If you used that subnet mask, then
192.168.0.50 would not be able to talk to
192.168.0.150 because those addresses would be on different networks. The boundary of the network does not align with a dot in the address. It is not nearly as intuitive to humans, which is why you don't ever see it being used.