Hi everyone,
Does anyone know how to fix a "semi-bricked" nvr caused by updating from very old firmware straight to latest one? I found out I should not update firmware like that the hard way.
My NVR is DS-7604NI-E1/4P which ran firmware v3.3.4 build 160118 when I received it. I updated it to the latest ones v3.4.106 Build191009 through web interface successfully and I was able to create password and pattern. However, after restart the pattern doesn't work, user name drop down list is blank and un-clickable.
I went through this forum and here is the list of what I did:
TFTP using hikvision tftp tool: unsuccessful with econt-vision-av2000 failed message.
TFTP using Scott Lamb python script on window laptop: unsuccessful with same econt-vision-av2000 failed message.
TFTP using Scott Lamb python script on linux laptop: no response or message from nvr. I used command line "sudo tcpdump -i eth0 -vv -e -nn ether proto 0x0806" and the result showed that my nvr only look for itself and my router ip address, not the tftp server address of 192.0.0.128: "Request who-has 192.0.064 tell 192.0.064, length 46, Request who-has 192.168.50.254 tell 192.0.0.64, length 46". I think since my nvr is only semi-bricked and can still boot, it does not switch to recovery mode and look for tftp server?!
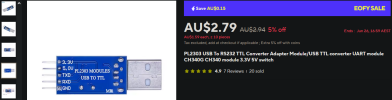
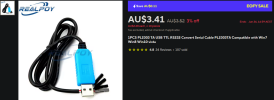
If anyone can suggest me other methods to fix this I would really appreciate. In the mean time, I have ordered some PL2303 and PL2303TA cables to serial into my nvr if all other method fail. Hope I ordered the correct one since I have not done this before.
Does anyone know how to fix a "semi-bricked" nvr caused by updating from very old firmware straight to latest one? I found out I should not update firmware like that the hard way.
My NVR is DS-7604NI-E1/4P which ran firmware v3.3.4 build 160118 when I received it. I updated it to the latest ones v3.4.106 Build191009 through web interface successfully and I was able to create password and pattern. However, after restart the pattern doesn't work, user name drop down list is blank and un-clickable.
I went through this forum and here is the list of what I did:
TFTP using hikvision tftp tool: unsuccessful with econt-vision-av2000 failed message.
TFTP using Scott Lamb python script on window laptop: unsuccessful with same econt-vision-av2000 failed message.
TFTP using Scott Lamb python script on linux laptop: no response or message from nvr. I used command line "sudo tcpdump -i eth0 -vv -e -nn ether proto 0x0806" and the result showed that my nvr only look for itself and my router ip address, not the tftp server address of 192.0.0.128: "Request who-has 192.0.064 tell 192.0.064, length 46, Request who-has 192.168.50.254 tell 192.0.0.64, length 46". I think since my nvr is only semi-bricked and can still boot, it does not switch to recovery mode and look for tftp server?!
If anyone can suggest me other methods to fix this I would really appreciate. In the mean time, I have ordered some PL2303 and PL2303TA cables to serial into my nvr if all other method fail. Hope I ordered the correct one since I have not done this before.