Hi guys,
I'm looking for some advice to separate my network, so my normal LAN doesn't get affected by the traffic of my camera's.
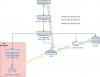
I'm running a VMS server with 13 camera's. My network setup is like:
ISP->Router->Main switch -> POE camera switch -> 13 camera's
How do I prevent that the data of those camera's goes through the router so it affects my normal LAN. I do have some networking knowledge, like subnetting, creating VLAN's etc but it seems I miss some basic knowledge... haha
I'm looking for some advice to separate my network, so my normal LAN doesn't get affected by the traffic of my camera's.
I'm running a VMS server with 13 camera's. My network setup is like:
ISP->Router->Main switch -> POE camera switch -> 13 camera's
How do I prevent that the data of those camera's goes through the router so it affects my normal LAN. I do have some networking knowledge, like subnetting, creating VLAN's etc but it seems I miss some basic knowledge... haha