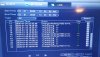
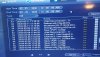
I think I was hacked?
- Thread starter ponyrider127
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
area651
Getting comfortable
From just looking at that, it looks like it. I'd guess its time to disconnect everything, perform factory resets on everything that you can and then set it all up with new passwords.
I would seriously doubt that some nefarious character was sitting there "self juicing" (Cohen reference from The Dictator) for 5mos while watching your cameras. More likely is that they've been mining bitcoin or attacking other stuff.
I would seriously doubt that some nefarious character was sitting there "self juicing" (Cohen reference from The Dictator) for 5mos while watching your cameras. More likely is that they've been mining bitcoin or attacking other stuff.
tigerwillow1
Known around here
Are you concerned with the tampering alarms? My understanding is that these are meant to indicate physical tampering with a camera. I don't think it has anything to do with network traffic.
bigredfish
Known around here
Those are not anything serious, I see them all the time, except for the p2p errors because I never use them, looks like a unexpected reboot and with those NVR's it is expected at times, check your account logs and the details to see who and when people were logging in. Default the networking and disable P2P, change PW. A outside login should log be a entry, and you should see the IP Address, unless someone hacked your network locally.
Last edited:
I get tampering logs sometimes on closed systems, not sure what triggers them but its usually 1 or 2 cams that are triggering them, best guess would be a disconnect.Are you concerned with the tampering alarms? My understanding is that these are meant to indicate physical tampering with a camera. I don't think it has anything to do with network traffic.
tigerwillow1
Known around here
You Get the cigar @tigerwillow1There's a bit of chinglish description for the tampering alarms in the NVR and camera manuals. My take on it is that it's an algorithm to detect an attempt to disable the camera view, such as covering the lens.
Tampering. When someone viciously masks the lens, or the output video is in one-color due to the environments light change, the system can alert you to guarantee video continuity. You can enable “Alarm output “or “Show message” function when tampering alarm occurs.
I think in my cases, it could have been spider webs or color changes, Most of the cams were up high enough, and where they were I do not believe people would be messing with them in that manor. Learn something new every day here.
Chris,
Sorry to see this but you encountered some remote logins. line 53 and 54 on log.
Suggest that you use an IP intrusion tool or just simple exception to allow your remote IP to connect. Check your router setting and add your remote IP (incoming blocking connections).
Secondly, change the port that the device uses for video, http and remote config, DONT use DMZ !!!! as there is software available to scan the internet for broadcasts from the known ports of Video devices.
Good luck
Sorry to see this but you encountered some remote logins. line 53 and 54 on log.
Suggest that you use an IP intrusion tool or just simple exception to allow your remote IP to connect. Check your router setting and add your remote IP (incoming blocking connections).
Secondly, change the port that the device uses for video, http and remote config, DONT use DMZ !!!! as there is software available to scan the internet for broadcasts from the known ports of Video devices.
Good luck
I would recommend not opening ports at all and look into setting up a VPN. Plenty of how-to information on this site.
Line 53 and 54 are your cameras establishing connection to the NVR after a reboot. In This case it was a abnormal reboot, 0x01: Abnormal reboot: power loss, system crash, or other undefined abnormality. All the rest of everything in that log would be expected after a reboot, If the system was hacked and actually got logged into and settings were normally saved and changed, they would do a "Normal reboot" if it was purposely restarted.Chris,
Sorry to see this but you encountered some remote logins. line 53 and 54 on log.
Suggest that you use an IP intrusion tool or just simple exception to allow your remote IP to connect. Check your router setting and add your remote IP (incoming blocking connections).
Secondly, change the port that the device uses for video, http and remote config, DONT use DMZ !!!! as there is software available to scan the internet for broadcasts from the known ports of Video devices.
Good luck
0x00: DVR has rebooted normally: routine maintenance reboot or a user reboot. These were taken from the Dahua Wiki.
DahuaWiki
Last edited:
Sorry its been awhile. Making face masks non stop.
Ok everyone here is where I'm at. Reset all and with new passwords. Set up VPN with a DD-WRT flashed Linksys E4200 that only stays connected for less than three min. I am learning as I go so be kind for a noob. One step forward two steps back it seams. What do you think I am missing or just bad router. I am using Smart PSS.
Thanks for all the input.
Ok everyone here is where I'm at. Reset all and with new passwords. Set up VPN with a DD-WRT flashed Linksys E4200 that only stays connected for less than three min. I am learning as I go so be kind for a noob. One step forward two steps back it seams. What do you think I am missing or just bad router. I am using Smart PSS.
Thanks for all the input.
So just so its clear what you are saying, is it dropping the VPN after 3 mins or are all of your clients on that router dropping if you have anything else setup on it. Is the Router New and was working fine before you flashed it?Sorry its been awhile. Making face masks non stop.
Ok everyone here is where I'm at. Reset all and with new passwords. Set up VPN with a DD-WRT flashed Linksys E4200 that only stays connected for less than three min. I am learning as I go so be kind for a noob. One step forward two steps back it seams. What do you think I am missing or just bad router. I am using Smart PSS.
Thanks for all the input.
The router was not new someone gave it to me I flashed it. I have two computers on VPN one WiFi and one wired for testing and both lose connection at the same time. It seams to be staying connected longer but will eventual drop connection. The WiFi computer will connect to my other non-VPN modem/router when connection drops and the wired will not reconnect on its own. I do not want my cameras on it until I know it will work.
It's been awhile. I now have a asus router with VPN setup behind a modem/router on it's own network and is working great. So now for the next phase to view remotely. It seems that everything I read says DO NOT PORT FORWARD. I have an account with DYNDNS they also want you to port forward. So what do I need to do or go to find out how to view remotely.
Thanks for all of your input.
Thanks for all of your input.
fenderman
Staff member
- Mar 9, 2014
- 36,891
- 21,407
You need to use the VPN to view remotely the fact that you set up the VPN does nothing until you actually connect to the VPN for remote viewing. If you port forward it defeats the entire purpose of the VPN because it’s actually doing nothing.It's been awhile. I now have a asus router with VPN setup behind a modem/router on it's own network and is working great. So now for the next phase to view remotely. It seems that everything I read says DO NOT PORT FORWARD. I have an account with DYNDNS they also want you to port forward. So what do I need to do or go to find out how to view remotely.
Thanks for all of your input.
Simple - turn on OpenVPN on your asus router and set it up and create a certificate and put the certificate on any device you want to use to remote in. Put OpenVPN on your remote device and you are good to go. I mean a few more steps than that LOL, but you can find that in the wiki above.