Tolting Colt Acres
Pulling my weight
- Joined
- Jun 7, 2016
- Messages
- 378
- Reaction score
- 153
I recently set up PiHole on my network. Reviewing the logs, I noticed my cameras, which were configured to use ntp (pool.ntp.org) were spamming the dns server every few seconds.
going to one of the cameras, I pull up the Time Settings page and verified my settings:
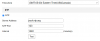
I had set this up years ago in my cameras, I use pool.ntp.org on all my servers on my network, and for my other machines, it works just fine...
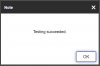
when I click on the "test" button, so ntp seems to be fine. Yet, according to my dns logs:
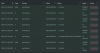
the cameras are spamming the DNS server every few seconds to resolve addresses.
I'm guessing this has something to do with IPv6, which is returning NODATA, and thus (perhaps) causing the cameras to repeatedly re-query the DNS server attempting to get an AAAA record.
Since there does not appear to be a way to disable IPV6 on the cameras, the only solution would appear to be to hard-code an ip address for an ntp server, which of course defeats the entire purpose of using an ntp pool....
going to one of the cameras, I pull up the Time Settings page and verified my settings:

I had set this up years ago in my cameras, I use pool.ntp.org on all my servers on my network, and for my other machines, it works just fine...

when I click on the "test" button, so ntp seems to be fine. Yet, according to my dns logs:

the cameras are spamming the DNS server every few seconds to resolve addresses.
I'm guessing this has something to do with IPv6, which is returning NODATA, and thus (perhaps) causing the cameras to repeatedly re-query the DNS server attempting to get an AAAA record.
Since there does not appear to be a way to disable IPV6 on the cameras, the only solution would appear to be to hard-code an ip address for an ntp server, which of course defeats the entire purpose of using an ntp pool....
