Anyone assist me with getting serial console going, on a nbd7024h-p
by Hangzhou Xiongmai Technology Co.
I updated the firmware, because the NVR gave me a message, update available with a pop up message saying update is available over the internet. I agreed but the NVR never came back, stuck on a reboot cycle. Shows the splash screen and reboots.
I do have a log of the start up from the serial console. Will post later, but it doesn't have much info, except Kernel is bad. (but no Tx to NVR)
I know the 3 pins that are Rx,Tx,ground.
I tested ground pin to common ground by ohm meter.
And getting the Rx and Tx is trial and error, because there are only 2 pins left.
One has infinite resistance and the other is 5kohms.
The voltage changes but is like 1.7v for both I think, will check again later.
When I connect the ground, I get garbled output on Putty. I use the 115200,8bits,no parity, no flow control, but I can change to 7bits,etc and it still works.
But the ground connection kills it. Becomes garbled/gibberish immediately.
But interestingly leaving Rx and TX connected I have visual output/log of boot up.
Or even moving the Tx to ground and keeping Rx connected on the NVR, but the ground wire to the TTL/USB makes it garbled, I tired 2 diiferent TTL/USB just in case it was damaged, so I don't believe so.
And pressing Ctrl+C doesn't nothing.
probably no output from my computer/keyboard to the NVR.
The log shows Ctrl+C as the command to issue to interrupt the boot, and it is uboot.
Anyone suggestions???
I read this very good thread,Longse LS-N3525D Bricked.
Longse LS-N3525D Bricked
I tried contacting bheremans, but no response received. I also tired contacting the NVR company
Hangzhou Xiongmai Technology Co.,LTD.-00000107(NBD7024H-P)firmware, but no response, all I have is there sales email from their website.
Any help/advise would be greatly appreciated. I searched all over can't find, much info on this serial console problem.
Sincerely,
Jerry
by Hangzhou Xiongmai Technology Co.
I updated the firmware, because the NVR gave me a message, update available with a pop up message saying update is available over the internet. I agreed but the NVR never came back, stuck on a reboot cycle. Shows the splash screen and reboots.
I do have a log of the start up from the serial console. Will post later, but it doesn't have much info, except Kernel is bad. (but no Tx to NVR)
I know the 3 pins that are Rx,Tx,ground.
I tested ground pin to common ground by ohm meter.
And getting the Rx and Tx is trial and error, because there are only 2 pins left.
One has infinite resistance and the other is 5kohms.
The voltage changes but is like 1.7v for both I think, will check again later.
When I connect the ground, I get garbled output on Putty. I use the 115200,8bits,no parity, no flow control, but I can change to 7bits,etc and it still works.
But the ground connection kills it. Becomes garbled/gibberish immediately.
But interestingly leaving Rx and TX connected I have visual output/log of boot up.
Or even moving the Tx to ground and keeping Rx connected on the NVR, but the ground wire to the TTL/USB makes it garbled, I tired 2 diiferent TTL/USB just in case it was damaged, so I don't believe so.
And pressing Ctrl+C doesn't nothing.
probably no output from my computer/keyboard to the NVR.
The log shows Ctrl+C as the command to issue to interrupt the boot, and it is uboot.
Anyone suggestions???
I read this very good thread,Longse LS-N3525D Bricked.
Longse LS-N3525D Bricked
I tried contacting bheremans, but no response received. I also tired contacting the NVR company
Hangzhou Xiongmai Technology Co.,LTD.-00000107(NBD7024H-P)firmware, but no response, all I have is there sales email from their website.
Any help/advise would be greatly appreciated. I searched all over can't find, much info on this serial console problem.
Sincerely,
Jerry






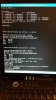
 I did a lot of googling today and not much was discovered on the kernel.
I did a lot of googling today and not much was discovered on the kernel.